
In a courtroom, the difference between conviction and acquittal often hinges on one critical factor, the integrity of digital evidence. Imagine a high-profile case where a piece of video footage proves someone’s innocence, but the defence challenges it, claiming the file was altered or handled improperly. Without a clear chain of custody, even the most compelling video or audio evidence can be rendered inadmissible, weakening an entire case.
The chain of custody refers to the documented process that tracks how evidence is collected, handled, stored, and transferred from one person to another. It is the legal backbone that assures courts that digital evidence remains authentic and untampered. Video and audio recordings play a decisive role in both criminal & civil cases, maintaining this chain is more complex than ever.
Every piece of digital evidence, from surveillance footage to recorded interviews, passes through multiple stages of handling. Each stage introduces potential risks such as file corruption, unauthorised access, or metadata loss. These issues are magnified when evidence is edited, redacted, or transferred across different systems. As a result, law enforcement agencies, legal professionals, and forensic teams are turning to legal technology solutions designed to safeguard evidence integrity throughout its lifecycle.
This article explores why the chain of custody is essential for video and audio evidence, the legal implications of mishandling it, and how modern technology certifies authenticity, compliance, and trust in the courtroom.
At its core, the chain of custody is a continuous record of who collected evidence, when and where it was collected, how it was handled, and by whom it was transferred. Every action must be documented to make sure that no opportunity for tampering or contamination exists.
Key elements include:
Unlike physical evidence, digital files are easily duplicated and modified. Video and audio evidence add another layer of complexity. Files may be transcoded, compressed, or exported in new formats, often stripping metadata or altering timestamps.

For example, a smartphone video captured in .MOV format might be exported as .MP4 from a video management system (VMS). During this conversion, GPS metadata, time zone information, or even frame rate consistency can be lost. Such discrepancies may later invite questions about authenticity.
To illustrate, imagine two versions of a police interview recording, one exported directly from a dashcam, another converted by a third-party tool. If the latter lacks the original metadata, its credibility can be challenged.
Courts rely on specific rules and standards to determine admissibility. In the United States, Federal Rule of Evidence 901 requires that evidence be authenticated by
“sufficient proof that it is what the proponent claims.”
Maintaining an unbroken chain of custody is the primary way to meet this requirement. Guidance from the National Institute of Standards and Technology (NIST)
ISO/IEC 27037 further details best practices for handling digital evidence, emphasising integrity verification, documentation, and secure storage.
In any jurisdiction, the admissibility of evidence rests on authentication. Courts require proof that the evidence presented is original, complete, and unaltered. The chain of custody serves as this authentication backbone.

When digital evidence, especially video or audio, is presented, judges assess not only what the recording shows but how it was preserved. Each handler in the chain must be identifiable, and the process verifiable. Without that, even compelling evidence may carry little weight.
A single undocumented transfer or missing timestamp can create doubt. In some cases, that doubt is enough for exclusion. Courts may deem the evidence inadmissible or assign it less weight, weakening prosecution or defence arguments.
Legal outcomes have demonstrated this repeatedly:
Beyond exclusion, a broken chain can lead to appeals, mistrials, or case dismissals, wasting months of legal effort. Defence teams frequently exploit these weaknesses, asking, “Who touched this file, and when?”
Different legal systems apply varying standards:
These distinctions matter when evidence crosses borders or is shared with external agencies. Improper redaction without custody tracking can lead to both evidentiary and privacy violations.
Judges typically look for four markers:

Modern legal technology provides tools that help enforce integrity automatically. Essential controls include:
Metadata holds vital contextual information, creation date, GPS coordinates, frame rate, codec type, and device ID. Yet this data is fragile. Re-encoding or editing a file may strip it unintentionally. Robust digital evidence systems preserve metadata automatically and record any transformations.
Destructive redaction overwrites data permanently, often compromising the chain of custody. Non-destructive redaction, on the other hand, masks sensitive content while keeping the original intact. Tools that log each redaction step, version, and handler build transparency and defensibility.
The rise of deepfakes and AI-generated alterations challenges traditional authenticity checks. Courts now expect provenance validation, verifying file origin using content authenticity tools and cryptographic watermarking. Proactive teams adopt these technologies early to prevent disputes.
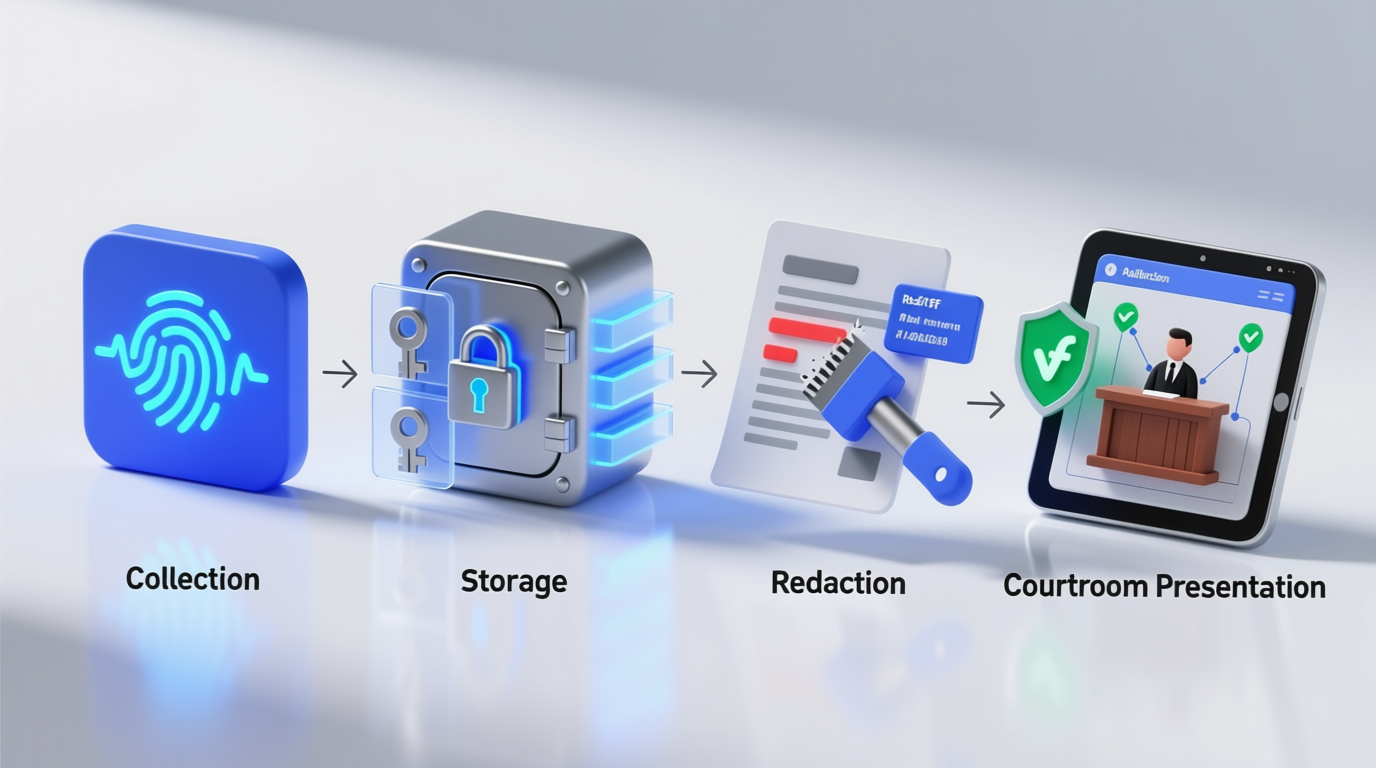
Step-by-step evidence management process:
In a 2022 federal fraud trial, investigators presented redacted surveillance video. The court accepted the evidence after reviewing the automated chain-of-custody and redaction reports, verifying that originals were preserved.
A law firm receives subpoenaed footage containing personally identifiable information (PII). Using a secure redaction workflow, they redact sensitive elements, generate a redaction report, and attach integrity hashes before submission. This make sure compliance with privacy laws and prevents admissibility disputes.
These cases illustrate a simple truth: transparency protects credibility. When every edit, redaction, and transfer is logged and verifiable, evidence can withstand even the toughest scrutiny.
As law enforcement adapts AI-powered security systems, ensuring data privacy becomes just as important as threat detection. This is where Sighthound Redactor and edge AI cameras provide a key advantage, offering cutting-edge safety without compromising student rights.
Key Features & Benefits
AI is not just a tool for surveillance; it's a catalyst for securely handling digital evidence. When deployed with privacy in mind, AI systems can detect threats early, automate critical responses, and create peace of mind for families and prosecution..
Those who embrace AI redaction will secure efficiency, compliance, and public trust.
Want to learn more about AI-powered redaction & digital evidence compliance? Try Sighthound Redactor today.
Want more insights? Read our AI-powered redaction best practices.
For business opportunities, explore our Partner Program today.
Published on: